Since the establishment of the public internet segment, privacy has been one of the major concerns. Virtual Private Networks (VPNs) are therefore in incredibly high demand, helping people achieve much-needed security and transparency when using the web. If you need to set up a VPN for your project, you have to choose a protocol. In this article, we consider the two most widespread ones – OpenVPN vs. IPsec – and evaluate which one is better.

VPN Security Challenges
Despite a broad range of advantages, any VPN comes with an array of issues. Consider the following:
- The level of security of a VPN connection is directly dependent on the security of authentication at the user end. Simple password protection methods are vulnerable to attacks and cracking. Two-, and sometimes three-factor identification may be necessary.
- VPN is based on remote access to the network, and every computer in the network must follow the same security regulations in order to avoid potential virus infection. High-quality anti-viral software can be used as a prevention technique.
- Split Tunneling. Initially, this concept is useful – it allows accessing both public and internal networks at the same time from a single computer. However, if you don’t put all of your traffic inside the VPN tunnel first, you create a breach for hackers to access your computer. This can be resolved by using a firewall.
OpenVPN Security and Use Details
When considering OpenVPN vs. IPsec, we should say that OpenVPN is more common. Many major VPN providers support this protocol – for example, NordVPN. It has been on the market for 17 years and is regularly updated and enhanced. The software is open-source; the key exchange is facilitated by SSL/TLS. It provides multi-layered protection via an authentication method that employs secure certificates and signatures at both ends of the connection.
Being one of the most popular modern security protocols, it is subject to malicious attention. Since it is open source, attackers can identify weaknesses in the system more easily. Nevertheless, they are held back by the network of IT specialists that constantly improve the protocol’s design.
Still, you should know about the most typical vulnerabilities that come with OpenVPN:
- TLS encryption has always been a weak link in the architecture of the protocol. It protects some of its unstable tools but can be susceptible to cyber-attacks unless packet compression is disallowed by the browser. Disabling it is the best way to avoid a range of hacker attacks on OpenVPN.
- HTTP websites can be controlled by hackers to implement a VORACLE attack. If you’re visiting an HTTP website through VPN, the attacker can intercept the decrypted data upon arrival. Luckily, most websites nowadays employ HTTPS – a safer, encrypted version of the protocol.
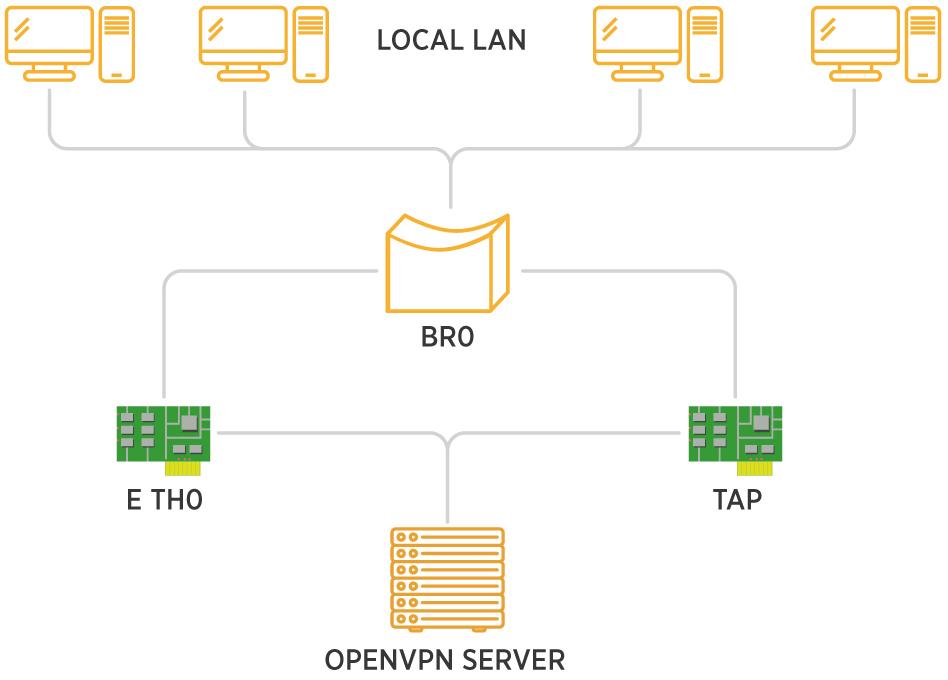
OpenVPN has conclusively been confirmed to have no major security issues. The mild and minor ones are being continually resolved and eliminated. In most cases, it is successfully implemented to provide access to company resources from remote locations. An exemplar is the case of SoftEther VPN, which employs several protocols, including OpenVPN. The software is particularly useful for endpoints behind firewalls and facility routers. The connection is camouflaged by HTTPS during deep packet inspection.
IPsec Security and Use Details
In an OpenVPN vs. IPsec comparison, the latter is definitely older. It has the advantage of being native to most operating systems, eliminating the need for third-party apps. It uses cryptography and mutual authentication to protect the data flow and internal communications in IP networks. Contrary to OpenVPN, which uses TLS and SSH encryption protocols at the top, seventh OSI layer (the application layer), IPsec operates at the third (network) layer.
As a set of security measures, IPsec is incorporated into the TCP/IP protocol. It provides means to ensure data integrity, confidentiality, and the correctness of the sender address and contains anti-replay mechanisms. It can also be employed to safeguard routers.
Nevertheless, IPsec is not without its own issues. There are two vectors upon which it can be compromised:
- Remote network access. Using remote access, computers joined to a corporate network can access the internal resources over the internet. Hence, there is a risk of getting the network infected by malware via the IPsec tunnel if the endpoint’s system was infected beforehand.
- Compromised algorithms. In recent years, hackers have deciphered some of the IPsec security algorithms. A way to avoid this is to use the latest algorithms that have not yet been reverse engineered.

OpenVPN vs. IPsec – Comparison
Aside from the different security characteristics, OpenVPN vs. IPsec protocols have a list of individual features. Here are the key ones to note:
- In contrast to IPsec, OpenVPN can be active in Ethernet tunnels.
- OpenVPN software is known to have user-friendly interfaces.
- OpenVPN runs easier diagnostics and has an overall more straightforward management system.
- Windows, Linux, and all other major operating systems have built-in IPsec variants, whereas OpenVPN is introduced through third-party applications.
- In site-to-site connections, OpenVPN functions faster and provides more security than IPsec.
- IPsec encryption operates on a kernel level, whereas OpenVPN functions in user space. Therefore, in terms of endpoint performance, IPsec is more favorable.
- With OpenVPN, you’re limited to the capacity of the software. IPsec can employ tools used for other firewall tasks.
Summary
So which one is better for you in the case of OpenVPN vs. IPsec? Well, they’re both great at specific jobs. For instance, OpenVPN will do well when you need fast site-to-site communication. However, beware of performance declines when using latency-sensitive apps – although this can be prevented via crypto acceleration, it is still a major burden to hardware.
Overall, OpenVPN should be used if you’re planning on accessing Ethernet, seeking better UI/UX, and working with site-to-site tunnels. Conversely, IPsec is more appropriate if you do not wish to get involved with third-party applications and are looking for something more universal. Additionally, it has better server-to-server performance and a broader range of available tools.
If you’re still not sure which protocol suits your project better, we can help you figure this out – contact us today for help and advice.