Only high-quality cybersecurity services can grant protection against unauthorized data access and malicious system intrusions. Any business acting through the web or proprietary software should be able to reinforce the protection against network and malicious software attacks as much as possible.
Intrusion detection and prevention systems (IDS) are used to identify activities that could breach security. However, most of the existing cybersecurity solutions are quite expensive and not rapid enough.
Free open-source NIDS solutions support deep packet inspection (DPI), so these are the best cybersecurity solutions today. At the professional level, the task is solved using complex solutions for assessment, analytics, and third-party risk management.
Why Your Business Needs Cybersecurity Professional Support
Gone are the days when simple firewalls and antivirus software were the only proper cybersecurity tools. Cyber threats can arise at any level. Global connectivity and the use of cloud services further increase risks. This makes cybersecurity services companies more and more in demand.
Sirin Software has extensive experience in network traffic analysis, best cybersecuritysolutions, and enhancements to existing products. For instance, we have added the HASSH function to Suricata, an open-source project with network traffic monitoring and intrusion prevention systems.
With its help, when setting up an SSH server, a unique combination of characters is created, which is checked by the computer on each connection. If you reinstall the SSH server, OS or replace the remote computer while keeping the address, the next time you connect, you will know about it.
Our cybersecurity masters have created several plugins for this IDS:
- Stenographer – provides full-server package download functionality.
- Testimony – guarantees easy integration with Suricata.
There are similar cybersecurity tools for Zeek. Deep packet inspection (DPI) IDS captures network event-related metadata. The Testimony plugin provides built-in support and has a single-machine multiprocessor architecture for AF_PACKET data exchange between processes.
Interesting Insights About Contributing to Suricata and Zeek
Plugins for version 6.0.0 of Suricata can be created for different types of package input and types of logging. They are written using the Rust or C languages. The first is used for cleaner code and easier multithreading. The latter is best used for low-level programming.
The output plugin can be used to work with warnings and all types of events ─ anomalies, protocol events, statistics. The main log output includes all JSON event and alert output. This makes it easy to integrate with Logstash and similar tools.
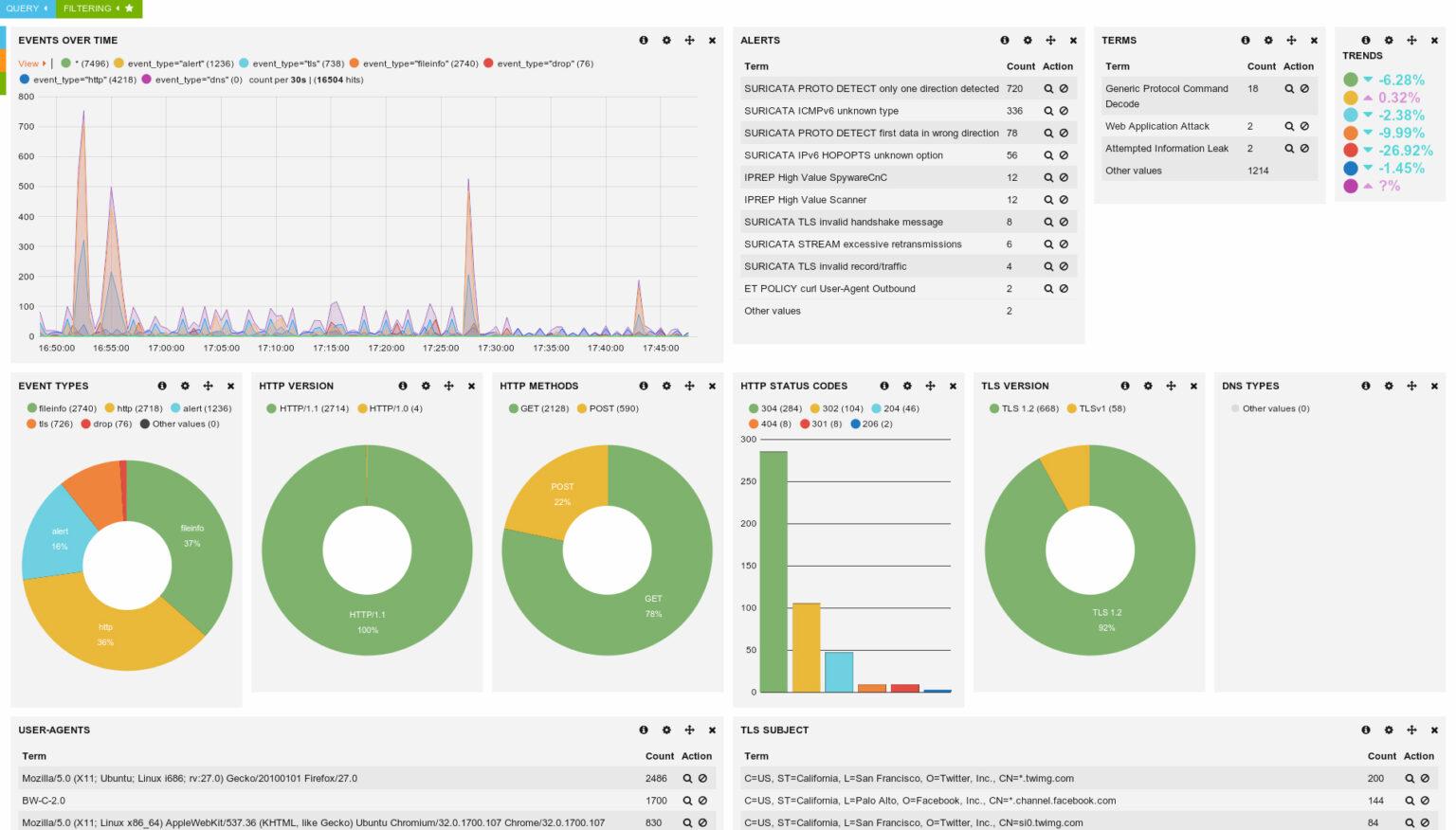
Based on network traffic monitoring, Zeek interprets and generates compact, accurate transaction logs and customizable output suitable for manual viewing on disk or SIEM.
IDS has a Zkg package manager. You can add your own package to the official list of plugins by specifying the package (plugin) repository link. At Sirin Software, cybersecurity masters have experience in deploying, configuring and testing Suricata and Zeek.
CyberSecurity. Why Does it Matter?
Cybersecurity is a section of information security that deals with the practice of protecting systems, networks, and programs from digital attacks and possible network threats.
The decision of the European Court of Justice Schrems II on the invalidity of the EU-U.S. Privacy Shield has added work to cybersecurity services companies. Implementation of security measures is complicated by the growing number of interconnected devices and the skill of attackers. Personal safety and privacy are at risk as criminals continue to attack the health and finance sectors.
In 2021, ransomware attacks will include not only ransom demands but also data breach threats. This will give a further push to the impact of the coronavirus, and the “work from home economy” will increase demand for sophisticated cybersecurity solutions for businesses.
Biggest data breaches
In 2011, hackers extracted data from over 24 million users from the Sony Online Entertainment gaming service and 77 million people from Sony PlayStation Network. In 2014, hackers got their hands on 100 terabytes of data from Sony Pictures’ clients.
Facebook is one of the leaders in terms of the number of leaks. As a result of the latter 2019 leak, due to the lack of sufficient cybersecurity solutions, the data of 267 million users leaked from the social network. For the same reason, in 2020, the data of over 200 million Instagram users became public!
How much it costs
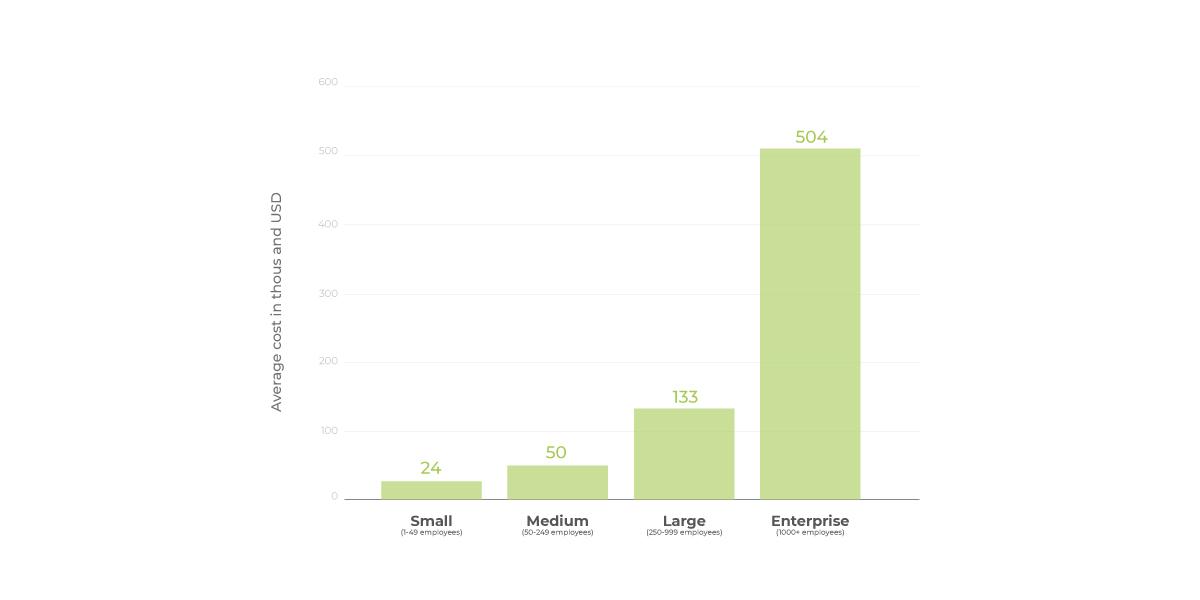
According to Accenture, from the first to the second quarter of 2020, the average ransom size increased by 60%, exceeding $178 thousand. About 43% of cyber attacks were aimed at small businesses, of which only 14% were using cybersecurity consulting services. According to Statista, the average cost of cyberattacks for firms with 250 to 999 employees was $133,000.
Best cybersecurity solutions
About 80% of cybersecurity issues are associated with known threats, which are easily identified by a signature-based rule system. Roughly 20% come from previously unknown threats that are most destructive and costlier. Therefore, Suricata/Zeek with deep packet inspection (DPI) are used for protection against both types of threats.
Problems With Open-Source Cybersecurity Solutions
The combination of Suricata and Zeek is very effective. The first can send a warning that the system has been compromised while the second can explain the incident and determine how other network communications are affecting.
Deeper view on Suricata/Zeek
Suricata quickly performs a network traffic analysis, using additional rules when new exploits are detected. IDS on a multithreaded architecture provides high-performance traffic inspection and handles many rules for high traffic volumes. Compatible with Snort’s extensive rule repositories and LUA support, it allows you to create advanced threat detection rules.
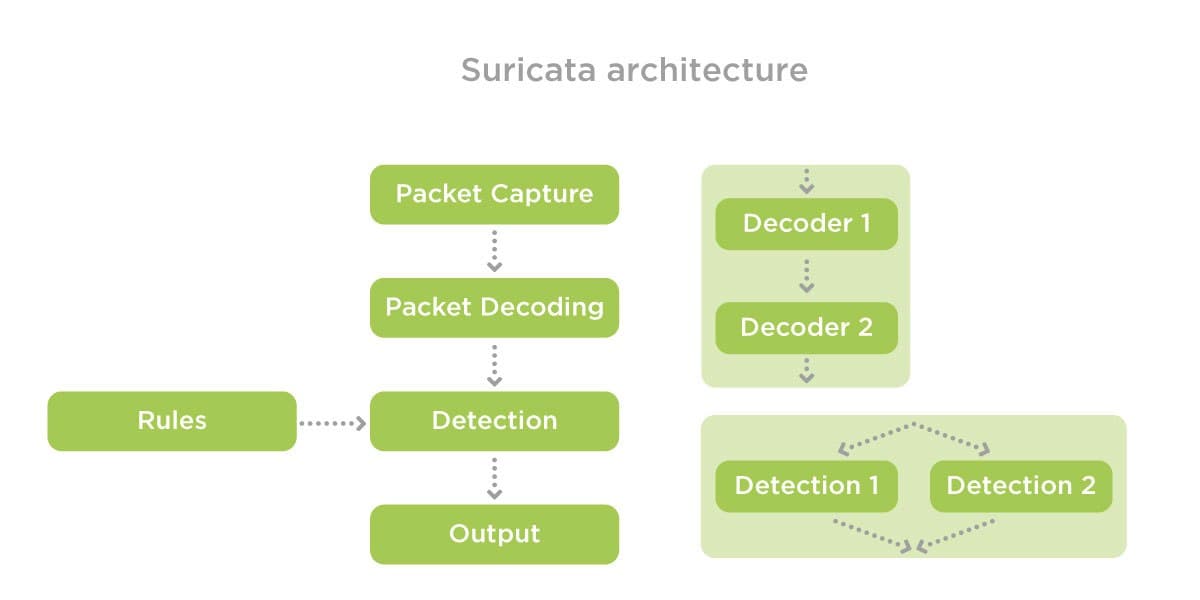
Zeek is designed for network traffic monitoring. The IDS monitors traffic flows and creates logs that record everything about network activity and other metadata useful for analysis.
Metadata can be searched, indexed, and queried in new ways that were not available with PCAP. A programming language structured like C++ can be used to compute numeric statistics, match against a regular expression pattern, and customize the interpretation of metadata.
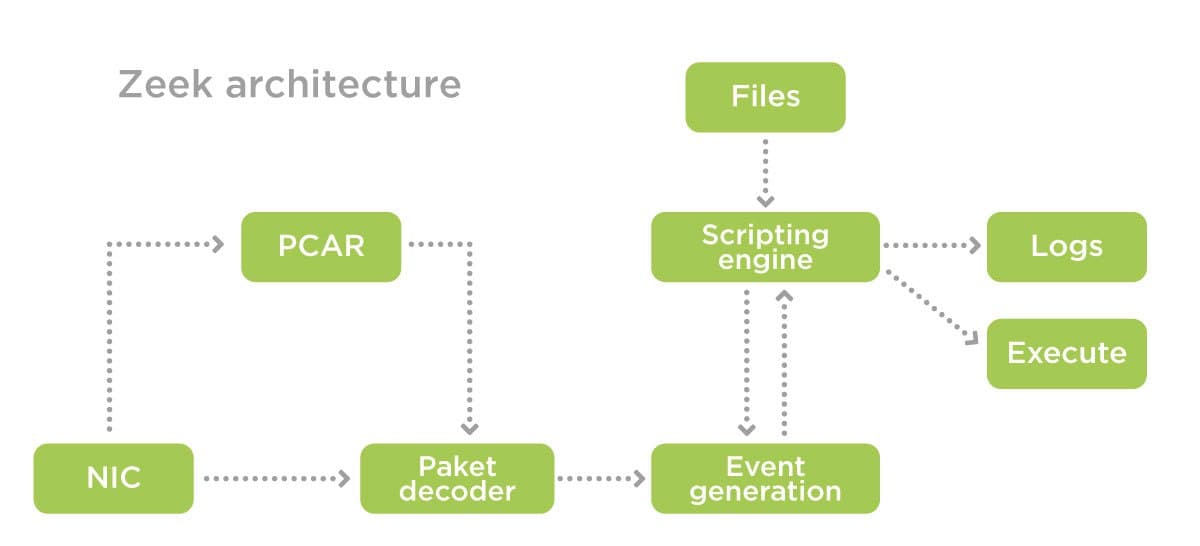
All in all, you should use both solutions:
- Suricata is more effective than Zeek in network traffic monitoring for known threats and sending alerts. Another benefit is that new threat data is often available in a Suricata-compatible format.
- Zeek provides the massive amounts of data needed for comprehensive visibility, network baseline, host and service profiling, passive anomaly, and threat detection.
You can rely on Suricata to quickly identify attacks whose signatures are readily available, and Zeek to provide the metadata and context needed for alert sorting and network traffic analysis. But there are difficulties:
- Zeek requires a vast infrastructure of hosts for different types of functions.
- The network traffic load is difficult to balance when the system is launched based on one host.
- Existing solutions (PF_RING_ZC) are difficult to set up and configure, and they also support few Intel network cards.
This is why we create and use custom plugins. Testimony is used as a solution to the problem of a large number of applications on one host, and Stenographer is used to save traffic.
Bottom Line
Tell Sirin Software about your data protection approach. We will provide quality cybersecurity consulting services, detect and prevent potential threats to your assets. You will receive a complete vision of the problems and effective cybersecurity services!
Apart from that, we hope the article helps figure out the specifics, capabilities, and general aspects of cybersecurity services for network administrators, security apps developers, CSOs, decision-makers, and online business owners.